
Table of Contents
- Code Quality and Build Settings
- System Architecture and Design
- Platform Interaction
- Network Communication
- Data Security
- Authentication and Session Management
- Cryptography
- Conclusion
Under Armour’s app, MyFitnessPal was hacked back in March 2018. An unauthorized party accessed data on its servers. There was no official statement concerning a leak of financial information. But, data from 150 million users was compromised in an instant.
Surprise, surprise!
You must be wondering, how could a global brand like Under Armour compromise on its app security?
Here, a thing…
A report by NowSecure showcases that 25% mobile apps today are vulnerable to serious attacks. We often share our Google and Facebook logins with third-party apps. We aren’t aware of their credibility most of the times, yet we share our personal details.
Now, the question arises…
Are they really safe as they say? Do they access only the information we’ve allowed permission to? Is my personal data safe out there? How do I trust an app when I’m sharing my personal and financial details?
You might have a few more questions. Today, we’re going to answer them. Today, we will create a checklist; a checklist that will comprehend your expertise in judging the apps out there.
We will start with the basics. Why is an app security a must? What are the issues and threats you can face?
We’ll agree on a point; mobile operating systems like Android and iOS are undoubtedly safer than the desktop systems. Android and iOS have internal basic encryption that protects most of your data. However, your data is vulnerable during a communication process.
Only when adherence is given to proper cryptography, your data will be safe. But, most app builders oversee this situation. They tend to over-rely on the OS’s cryptography, which is symmetrical in most cases.
Data transmitted without proper security is vulnerable to attacks. This data can be manipulated to access data in your phone and on servers. There are multiple ways to breach such information, which we will look at throughout the blog.
Cryptography is just one means to safeguard data. Breaching data is possible through various other means. You need to ensure that these threat windows are closed from all sides. How do you do that? Read through the blog to know more.
#1 Code Quality and Build Settings

No security can be of any help if the code is of poor quality. The following list compiles important pointers to keep a check on the code quality and its build settings.
App Provision:
- Ensure the app is properly signed and certified.
Release Mode:
- Validate if the app has been built in the release mode. It should have settings suitable for a release build.
Debugging:
- Confirm whether debugging and symbols have been removed and the app does not log debugging messages.
Exceptions:
- Identify if the app catches and handles exceptions.
Error Handling Logic:
- Validate access denial is set as a default for error handling logic.
Unmanaged Code:
- Ensure efficient usage of memory in unmanaged code.
Compiler Security Features:
- Identify the activation of security features such as stack protection and automatic reference counting, provided by the compiler.
Java Bytecode
- Validate the minification of Java bytecode.
#2 System Architecture and Design
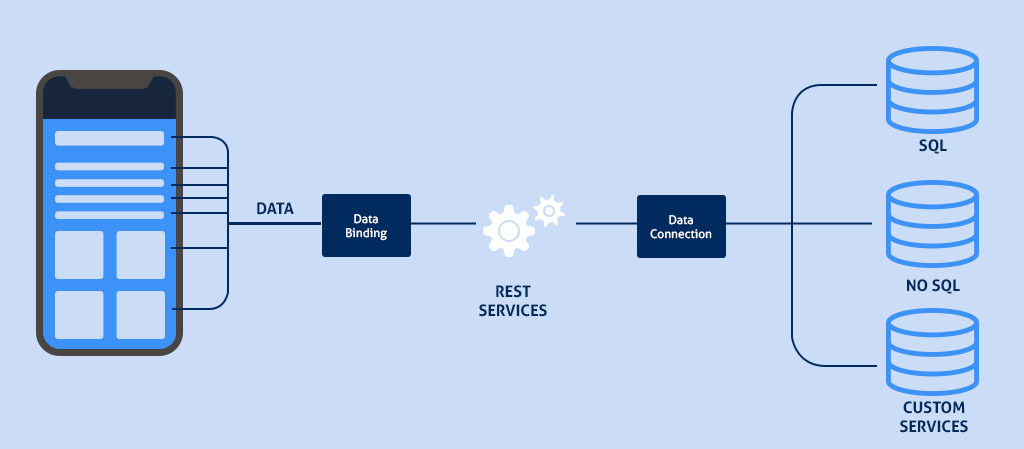
The architecture and design of your app is the most basic layer of security. Any loophole here can be exploited to break through the security and compromise data. Verifying the following points ensure a safe app usage.
Third Party Components
- Identify third-party components such as, libraries and frameworks, used by the application. Rectify its security implications.
- Perform a pre-requisite check on the third-party apps before implementation. Also, establish an inspection process every time the third-party app gets updated.
High-level Architecture and Connected Remote Services
- Authenticate the definition of a high-level architecture and its security features for the application and its remote services.
Application Components
- Identify the application components that will be used.
- Validate the definition of the application components for business and security functions.
- Ensure the identification of dependent components and their security implications.
Sensitive Data
- Identify sensitive data in the application
Security Controls
- Validate the security controls’ enforcement. Ensure its application on the client side and the remote endpoints.
- Certify a central implementation of the security controls.
Threat Model and Associated Remote Services
- Observe potential threats and its counters for the application and its remote services. Create a threat model around these observations.
Remote Endpoints
- Validate that the remote endpoints check if the connecting clients are using the updated version of the application.
Security Testing
- Tailor the configuration of the testing tools to the application. Ensure security testing is a part of the SDLC.
#3 Platform Interaction

Bugs can be injected to access sensitive data. It is important to follow a certain set of guidelines to ensure proper security at this stage.
Permissions:
- Establish the usage of mandatory set of permissions.
Validations:
- Ensure the validation of inputs from external sources. It includes data received via the User Interface and IPC mechanisms. Sanitize, if necessary.
Custom URL:
- Confirm the usage of proper mechanisms and secure it while exporting sensitive functions via custom URLs.
IPC Facilities:
- Ensure the app exports sensitive functions through IPC only of the mechanism is protected appropriately.
WebViews:
- Verify if JavaScript is disabled in WebViews unless required.
- Validate the allowance of the basic protocol handlers like HTTP. Restrict allowing handlers such as File, Tel, and App-id.
- Rectify if the app loads user-supplied resources into WebViews.
- Restrain if Java objects are exposed in a WebView. Only render script within the app package.
Object Serialization:
- Ensure the usage of object serialization with safe APIs.
Rooted or Jailbroken Device:
- Check if the executing device is rooted or jailbroken. In such cases, the user is warned, or the app terminates.
#4 Network Communication
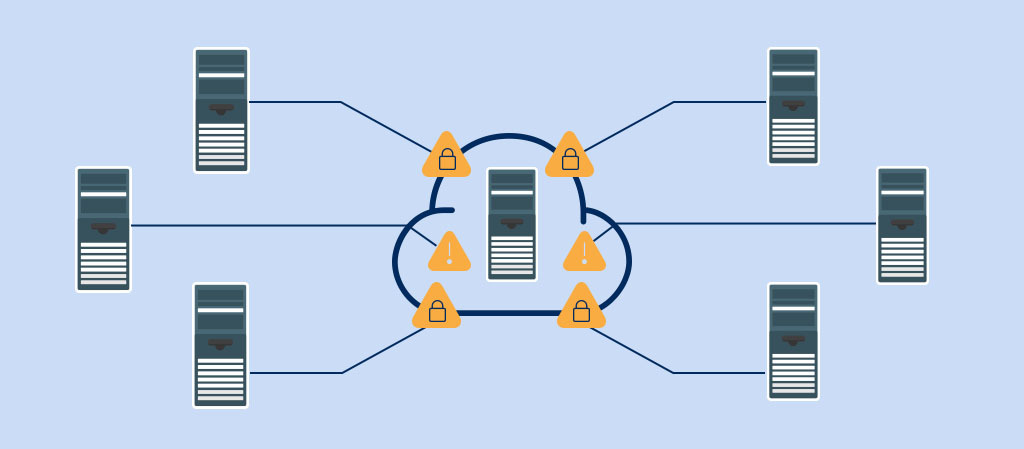
Your sensitive data is shared across the network while performing remote authentication. Leakage of such data can compromise any users’ identity.
Data Encryption:
- Ensure the consistent usage of TLS to encrypt data on the network.
TLS settings:
- Cross-check TLS settings with the best practices carried out in the industry.
Security Certificate:
- Establish the verification of the X.509 certificate of the remote endpoint during channel establishment. Accept certificates that are signed by a valid CA, only.
- Validate the application’s certificate usage. It should access certificates present in its store or pinpoints to the certificate or public key. Ensure it doesn’t establish connections with other certificates or keys.
Communication Channel:
- Check if the app uses secure communication channels for vital operations such as enrolment or account recovery.
#5 Data Security

It is crucial that you safeguard data at its source, that is, your phone. The following list compiles a list to safeguard data at the most basic level.
System Credential Storage
- Ensure the usage of cryptography and credentials to store sensitive data.
Sensitive Data
Keep a check on the following practices:
- Sensitive data is not written in the application log.
- Sensitive data is not shared with third-parties, except if necessary.
- Sensitive data is not exposed through IPC mechanism.
- Sensitive data is excluded from backup.
- Sensitive data, such as passwords and credit card numbers, is protected from screenshots or other data leaks.
- Keyboard cache is disabled for data sensitive text inputs.
- Clipboard is deactivated on data sensitive text fields.
- Application deletes sensitive data from View when switched.
- Application releases sensitive data in memory after a period of time. It clears memory after its use.
App Interface
- Educate the user about the best security practices for using the app. Identify and display the information that will be processed.
Device-Access-Security Policy
- Enforce a mandatory device access security policy like setting a device passcode.
#6 Authentication and Session Management

Sensitive data is accessed during authentication and to initiate sessions. It is vital that session and authentications are handled efficiently to ensure no leakage of data.
Access Tokens:
- Perform an authentication process (username/password, OTP) at the remote endpoint while providing remote services.
- Use randomly generated access tokens to authenticate client requests at the remote endpoint.
Remote Endpoint Session:
- Ensure session termination when you log out from the remote endpoint.
- Verify if the session terminates after a certain period of inactivity.
Password Policy:
- Check if a password policy is enforced at the remote endpoint.
Biometric Authentication:
- Ensure the usage of a biometric usage through unlocking a keystore or keychain.
Second Factor of Authentication(2FA):
- Verify the usage and enforcement of 2FA at the remote endpoint.
Step-up Authentication:
- Establish the usage of step-up authentication for sensitive data and transaction processes.
Login Activities Information:
- Verify if the application displays account activities, a list of devices used to access a particular account and allows the user to block certain devices.
#7 Cryptography
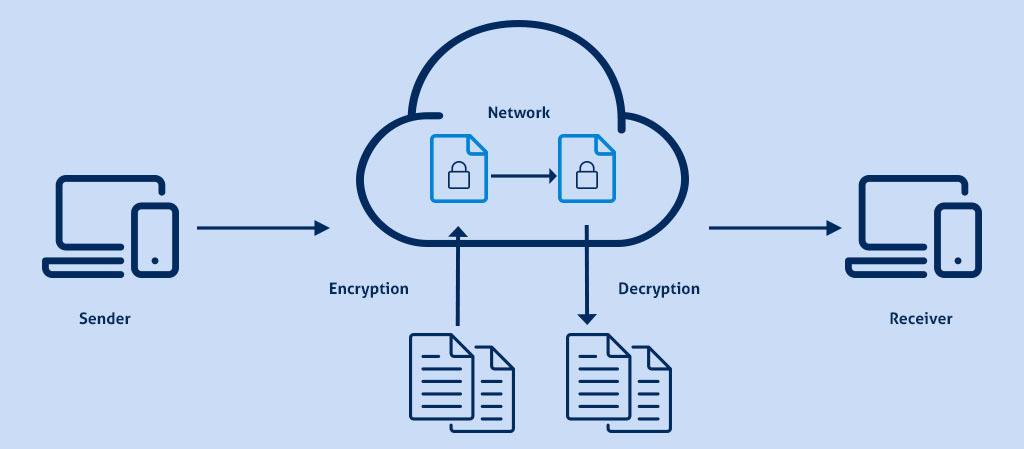
Safeguarding data without any cryptography is the same as ignoring the safety of your data. The following list compiles of a checklist necessary to use proper cryptography.
Symmetric Cryptography:
- Ensure the app doesn’t rely on symmetric cryptography as the only means of encryption.
Cryptographic Primitives:
- Check the usage of proven implementations of cryptographic primitives. Validate its configuration and usage to industry’s best practices.
Cryptographic Protocols:
- Vindicate the usage of only appreciated and recognised cryptographic protocols and algorithms.
Cryptographic Key:
- Validate the usage of different cryptographic keys for every process.
Random Values:
- Confirm that random values are generated using a secure random number generator.
Conclusion
At first, the list might seem exhaustive to you. But, owing to the technological advances and its ever-increasing complexity, this list just takes you over the basics of mobile app security. A new threat arises every day, and so does its countermeasures.
Following this checklist confirms that your mobile app will be safe from most vulnerabilities out there. Our team of experts at AlphaLogic ensure to update and secure ourselves and our consumers’ apps from the evolving intimidations caused due to app vulnerabilities.
Contact us instantly to ensure your app’s safety!
Dhananjay (DJ) Goel is the CTO at Alphalogic, passionate about technology, startups, game of thrones and coffee. He enjoys working on challenging problems with innovative startups.
